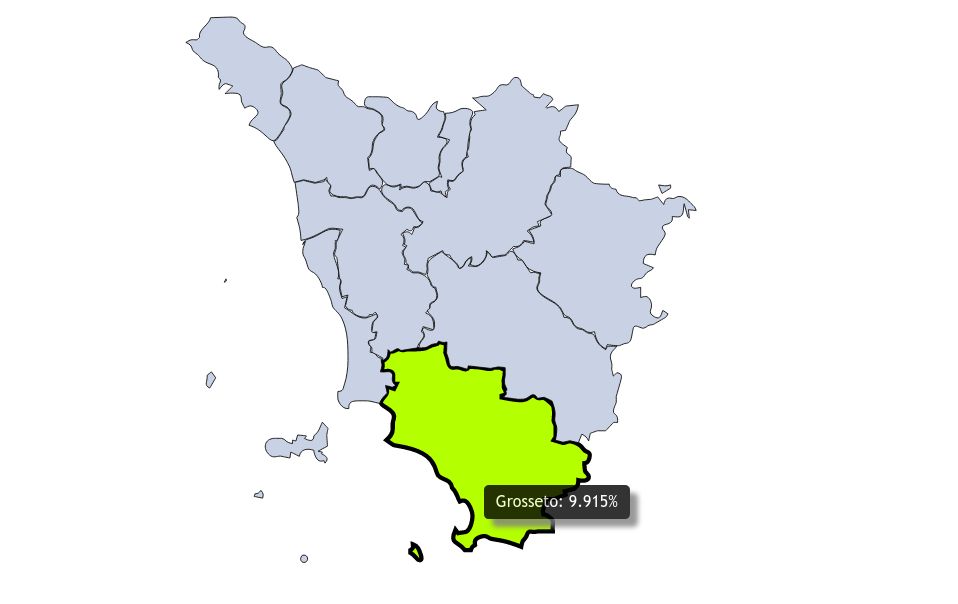
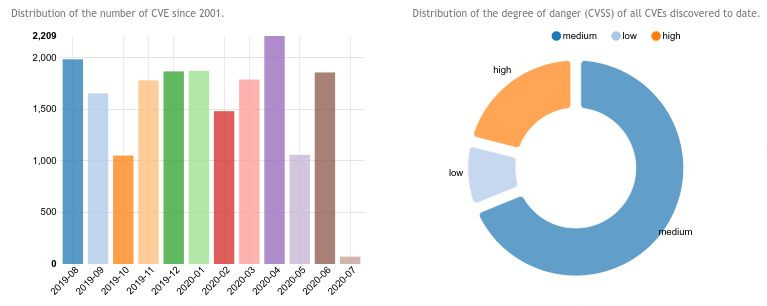
Pubblicato il nuovo Rapporto Nazionale PID Cyber Check, un’analisi approfondita sul livello di sicurezza informatica delle imprese italiane, basata su un questionario di autovalutazione promosso dall’Osservatorio sulla Cybersecurity. Il sondaggio, disponibile online, ha coinvolto 2.928 imprese e...
NOTIZIE & EVENTI
BLOG & VIDEO
SERVIZI
|
Servizio Rilevazione Malware. Il servizio permette di rilevare comportamenti malevoli in file (ad esempio, eseguibili o... |
Il servizio offre uno strumento semplice e rapido per l'autovalutazione per il calcolo del rischio cibernetico. Il... |
Il servizio offre una piattaforma che consente ai Registrar di verificare eventuali problemi di performance e sicurezza... |
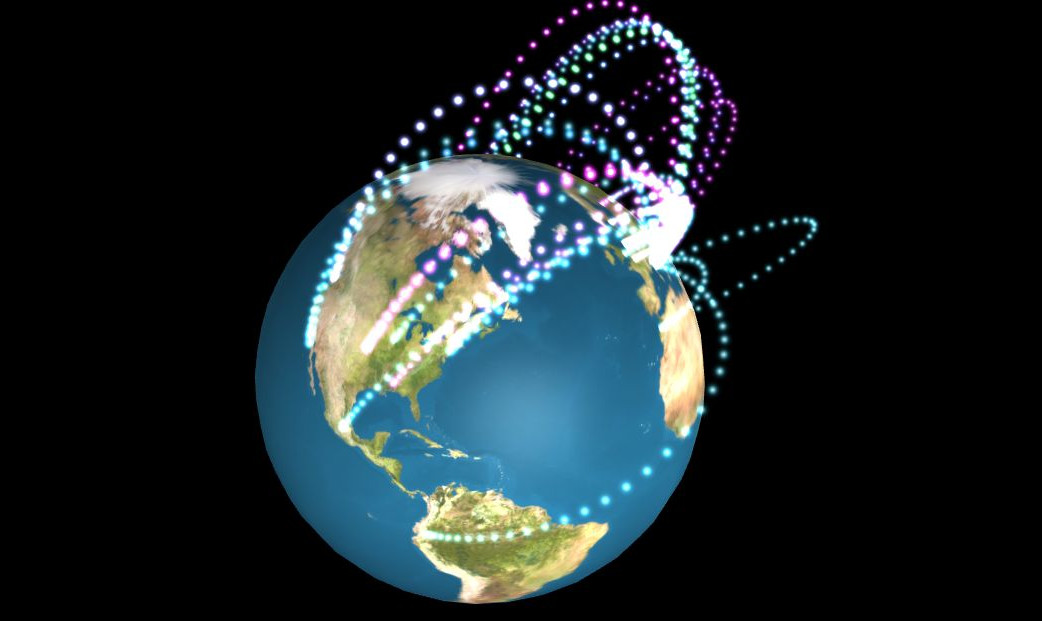
Il servizio mostra una rappresentazione 3D del traffico di rete relativo ad attacchi ad una honeypot a Pisa. Inoltre,... |