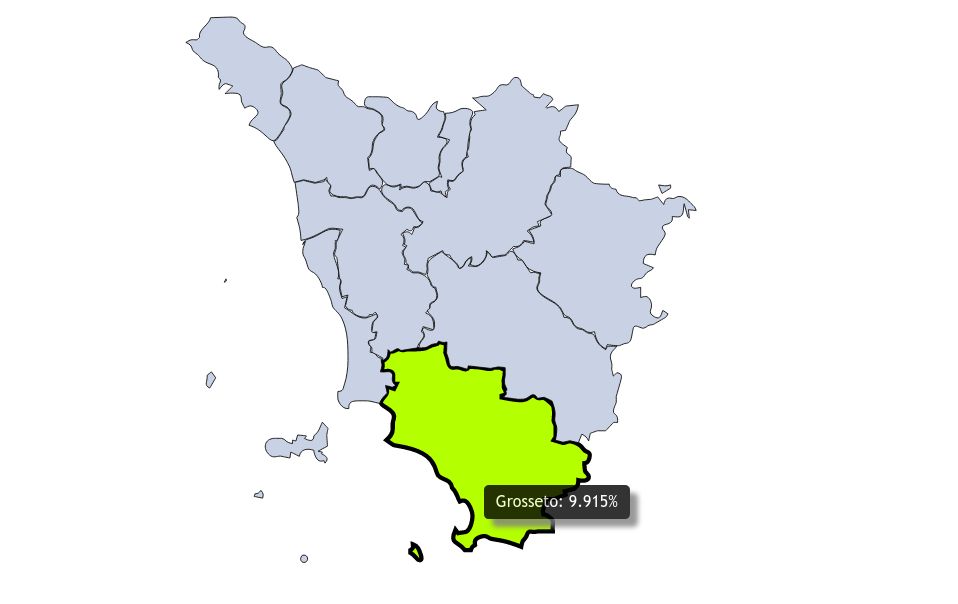
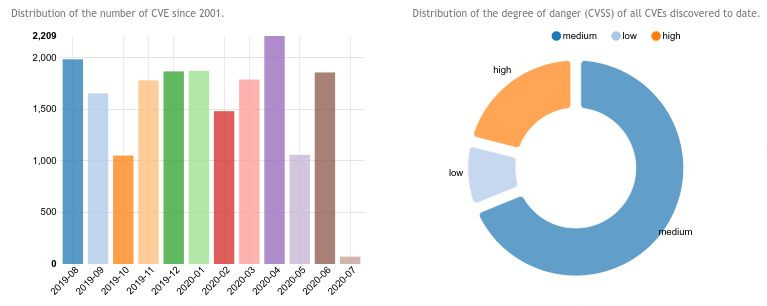
Pubblicato il nuovo Rapporto Nazionale PID Cyber Check, un’analisi approfondita sul livello di sicurezza informatica delle imprese italiane, basata su un questionario di autovalutazione promosso dall’Osservatorio sulla Cybersecurity. Il sondaggio, disponibile online, ha coinvolto 2.928 imprese e...
NOTIZIE & EVENTI
BLOG & VIDEO
SERVIZI
|
Un’ontologia rappresenta una risorsa per organizzare la conoscenza di un dominio in maniera più dettagliata attraverso... |
Il servizio analizza un log di richieste DNS e identifica se all’interno sono stati risolti dei nomi a dominio che... |
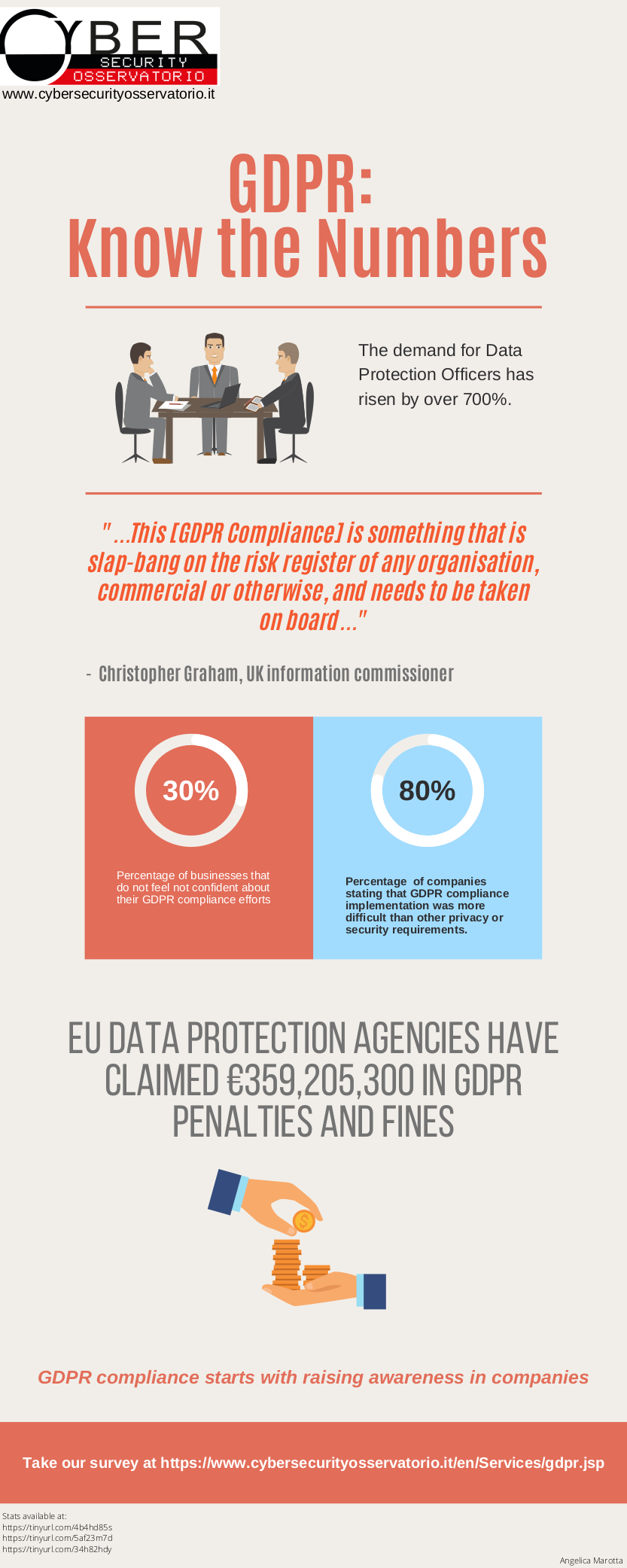
Il servizio offre un sondaggio per la verifica della conformità di un’organizzazione al GDPR (General Data Protection... |
Il Thesaurus offre una rappresentazione della conoscenza di un insieme di termini relativi alla Cybersecurity,... |