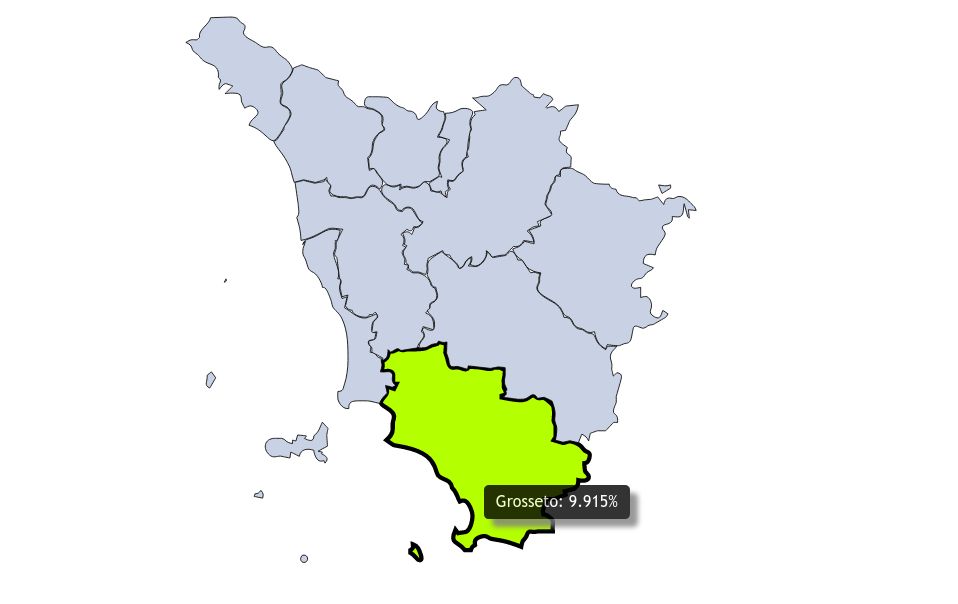
Pubblicato il nuovo Rapporto Nazionale PID Cyber Check, un’analisi approfondita sul livello di sicurezza informatica delle imprese italiane, basata su un questionario di autovalutazione promosso dall’Osservatorio sulla Cybersecurity. Il sondaggio, disponibile online, ha coinvolto 2.928 imprese e...
NOTIZIE & EVENTI
BLOG & VIDEO
SERVIZI
|
Il servizio utilizza una raccolta di tweet provenienti da utenti appartenenti a Twitter i cui tweet utilizzano parole... |
Servizio Rilevazione Malware. Il servizio permette di rilevare comportamenti malevoli in file (ad esempio, eseguibili o... |
Il servizio si prefigge di individuare comportamenti tipici dei ransomware quali, ad esempio, la cifratura di una... |
Il Thesaurus offre una rappresentazione della conoscenza di un insieme di termini relativi alla Cybersecurity,... |