Venerdì 11 ottobre 2024 si terrà l'ottava edizione del Cybersecurity Day, un evento organizzato dall'Istituto di Informatica e Telematica del CNR nell'ambito del progetto SERICS. La giornata sarà dedicata alle più recenti attività di ricerca e innovazione nel...
NOTIZIE & EVENTI
BLOG & VIDEO
SERVIZI
|
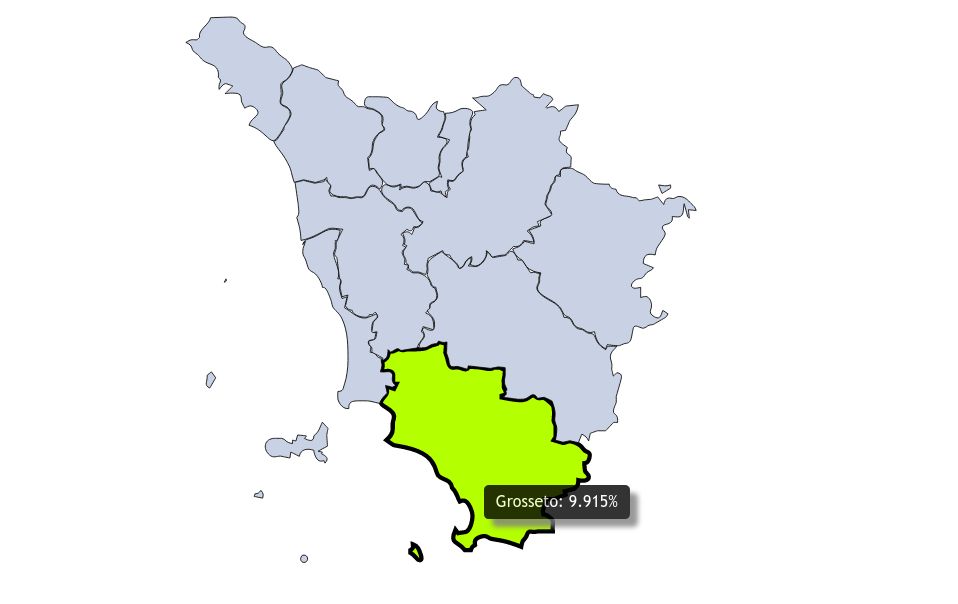
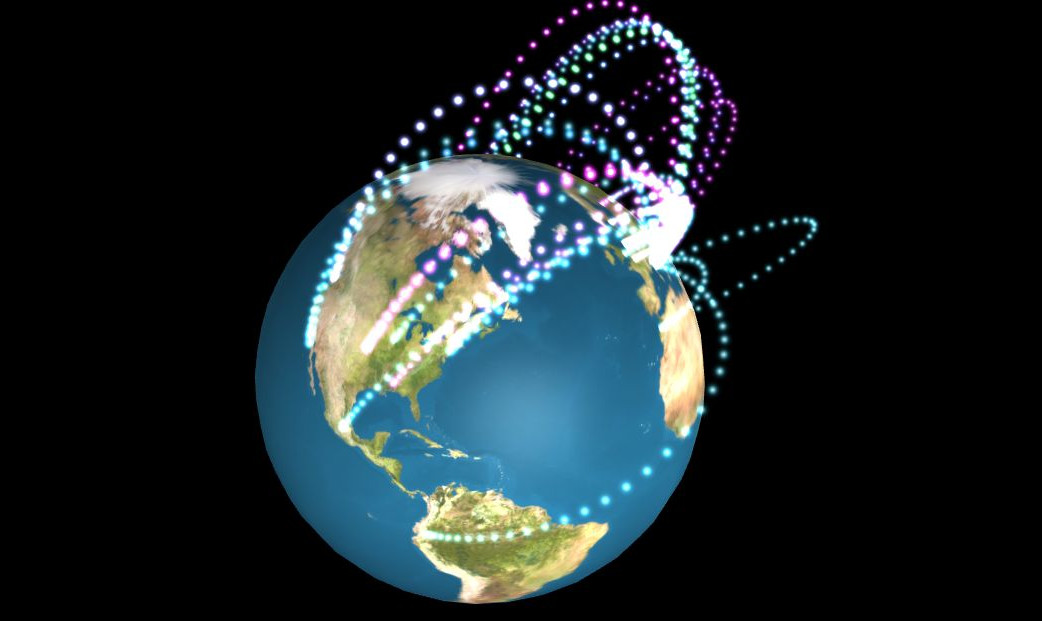
Il servizio mostra una rappresentazione 3D del traffico di rete relativo ad attacchi ad una honeypot a Pisa. Inoltre,... |
Il servizio analizza un log di richieste DNS e identifica se all’interno sono stati risolti dei nomi a dominio che... |
Il servizio offre una piattaforma che consente ai Registrar di verificare eventuali problemi di performance e sicurezza... |
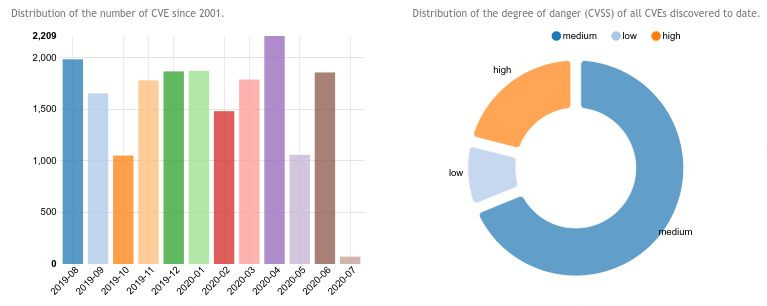
Il servizio raccoglie informazioni relative ad exploit pubblici aggiornati giornalmente attraverso il repository... |