Pubblicato il nuovo Rapporto Nazionale PID Cyber Check, un’analisi approfondita sul livello di sicurezza informatica delle imprese italiane, basata su un questionario di autovalutazione promosso dall’Osservatorio sulla Cybersecurity. Il sondaggio, disponibile online, ha coinvolto 2.928 imprese e...
NOTIZIE & EVENTI
BLOG & VIDEO
SERVIZI
|
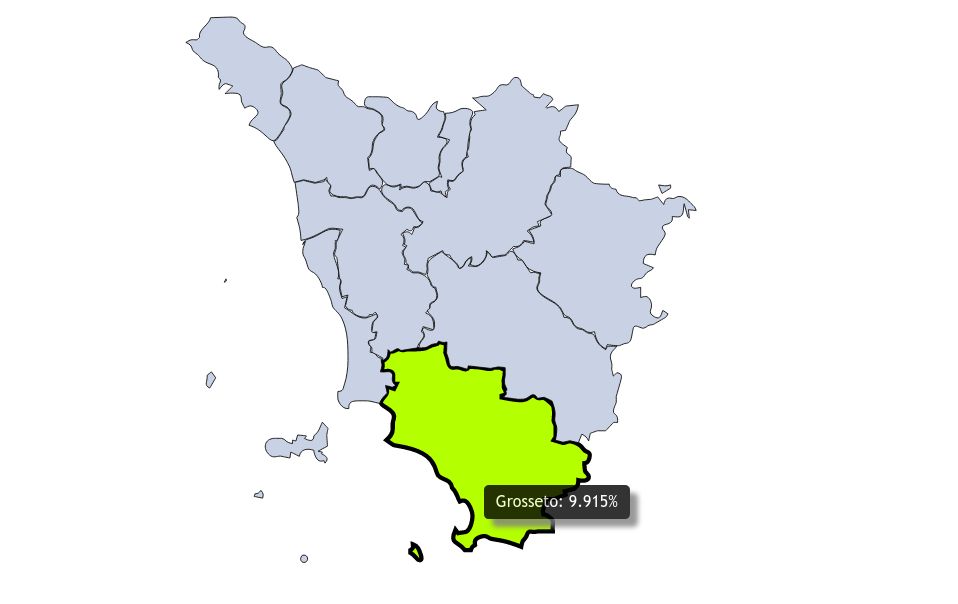
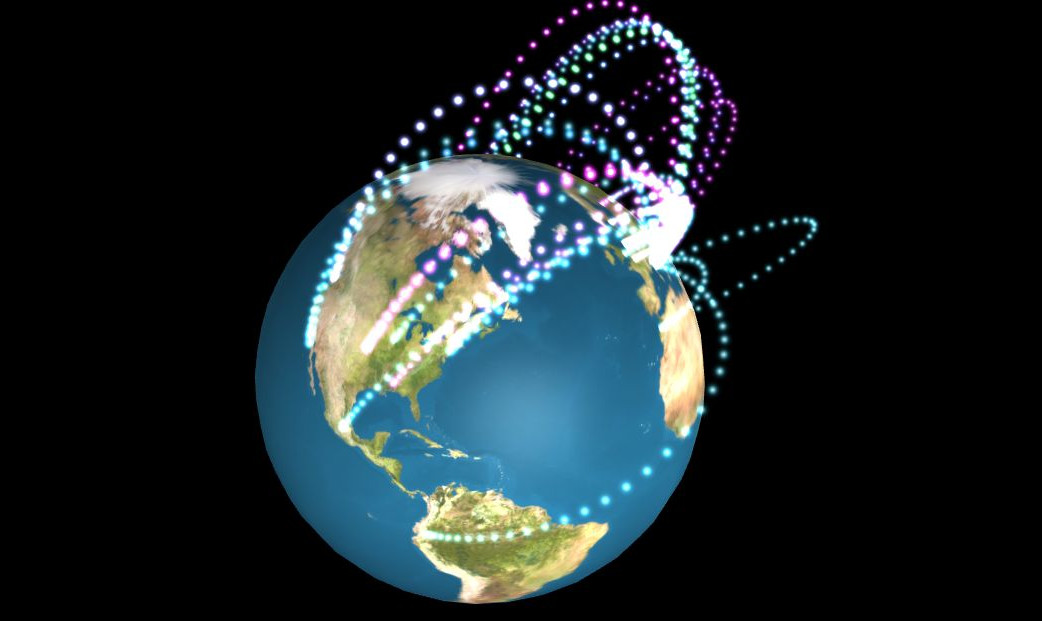
Il servizio mostra una rappresentazione 3D del traffico di rete relativo ad attacchi ad una honeypot a Pisa. Inoltre,... |
Il servizio utilizza una raccolta di tweet provenienti da utenti appartenenti a Twitter i cui tweet utilizzano parole... |
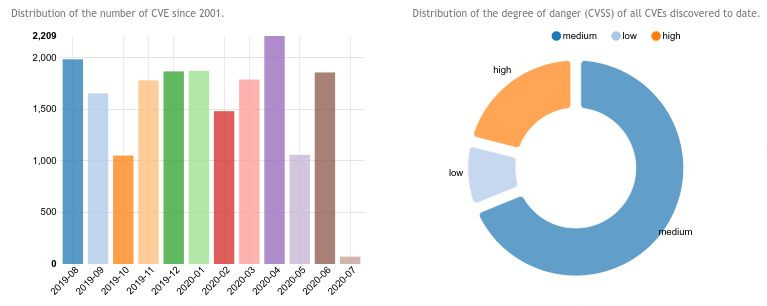
Il servizio offre la possibilità di cercare informazioni, note pubblicamente, relative a vulnerabilità di sicurezza... |
Il servizio raccoglie informazioni relative ad exploit pubblici aggiornati giornalmente attraverso il repository... |