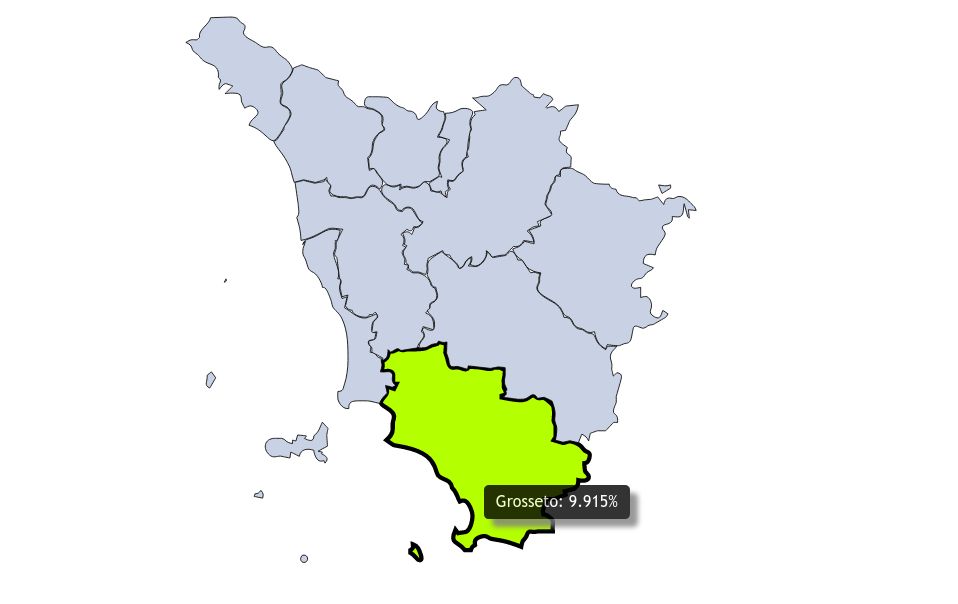
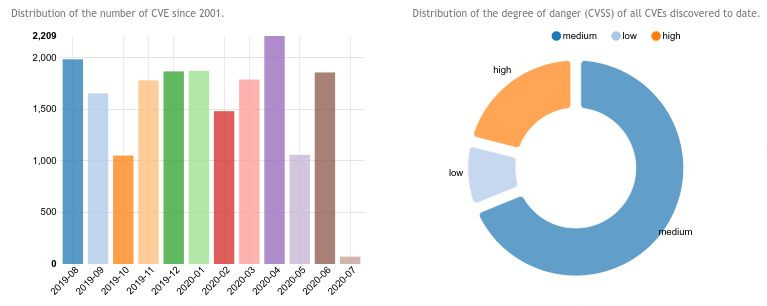
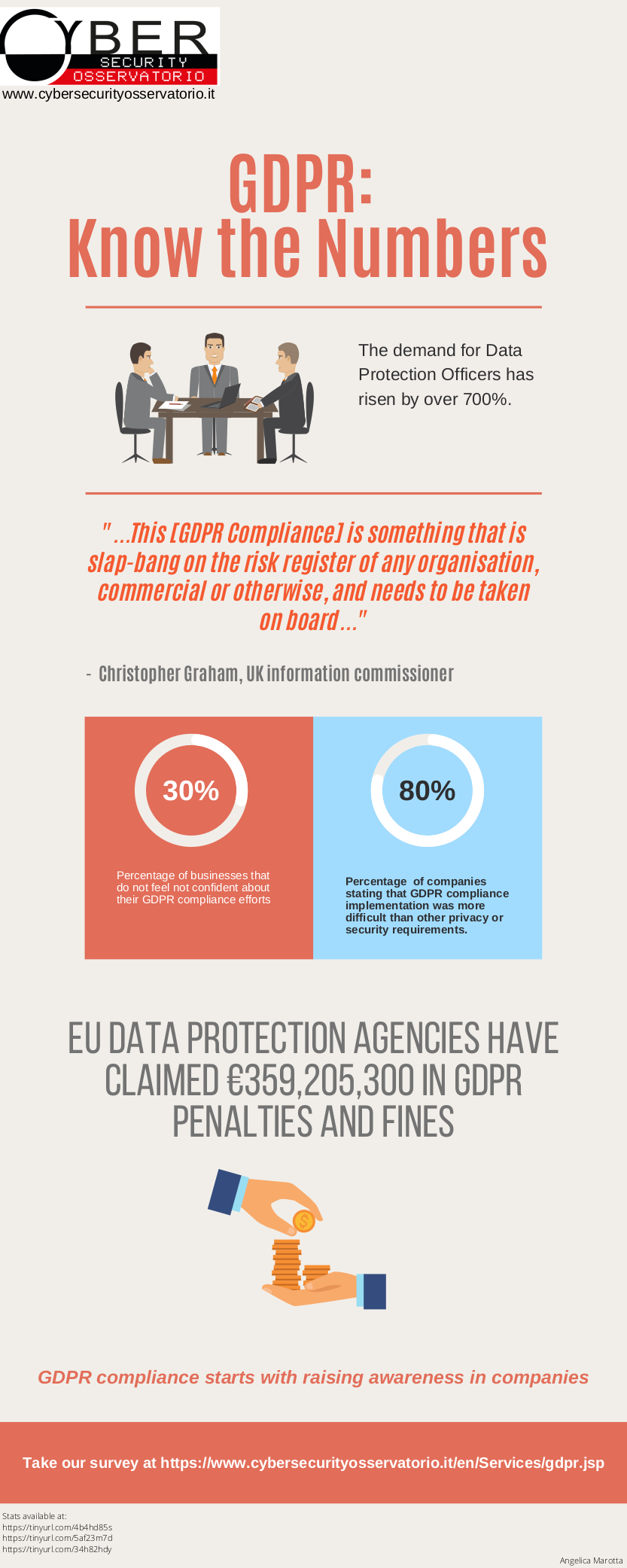
Pubblicato il nuovo Rapporto Nazionale PID Cyber Check, un’analisi approfondita sul livello di sicurezza informatica delle imprese italiane, basata su un questionario di autovalutazione promosso dall’Osservatorio sulla Cybersecurity. Il sondaggio, disponibile online, ha coinvolto 2.928 imprese e...
NEWS & EVENTS
BLOGS & VIDEOS
SERVICES
|
The main goal of the tool is to provide a simple and quick tool for cyber risk self-assessment. The tool requires two... |
This service analyses sets of email file in .eml format to identify the unsolicited ones (SPAM). Moreover, the service... |
This service offers the possibility of searching public domain information related to known security hardware and... |
This service shows statistics related to Tweets related to Cyber-Security, allowing to search them by keywords such as... |